16 billion credential leak: Google, Apple, Meta Users at Risk in June 2025
A massive June 2025 leak exposed 16 billion+ login credentials linked to Google, Apple, Meta, and more. Learn what happened, who’s affected, and how to protect your accounts from infostealer malware and session hijacks. #16 billion credential leak
Chain Editorial Team
6/21/20255 min read
💭 Imagine This…
You're sipping coffee, casually logging into your Gmail, when a strange alert pops up. “New login from Istanbul?”
You panic. You didn’t travel. You didn’t share your password. You didn’t even click any shady links lately.
What you didn’t know?
Last month, your browser auto-filled a password into a fake login screen crafted by malware. It silently scraped your session token, not just your password. That single click gave a hacker a master key and straight access to your account..
Welcome to the age of credential leaks without breaches.
A silent war where info-stealing bots, not brute-force attacks, dominate.
And the battlefield?
Your browser, your cookies, and now... 16 billion exposed entries.


⚡ FlashChain: Your 15s Brief
A colossal ~16 billion login entries just leaked from unsecured servers.
Data includes usernames, passwords, session tokens, cookies, many fresh and weaponizable.
Source: ~85% from infostealer malware, not direct platform hacks.
Affected indirectly: Google, Apple, Meta, Telegram, GitHub, and more.
Experts call it a blueprint for mass exploitation, not just a breach.
💡 Let’s Dive In
🌐 What Happened: The Massive 16B+ Credential Leak
In June 2025, cybersecurity researcher Bob Diachenko and Cybernews uncovered a shocking data breach:
30 unsecured datasets were found on open storage services like Elasticsearch and cloud buckets.
Together, they hold a staggering 16 billion entries of login info:
usernames, emails, hashed and plain-text passwords, session tokens, browser cookies, and device metadata.This includes credentials linked to Google, Apple, Meta (Facebook), Telegram, GitHub, and many others.
Let that sink in:
That’s 2x the population of Earth, meaning users likely appear multiple times in old and new forms.
🚨 Crypto Assets Now in the Crosshairs: How This Leak Puts Your Wallet at Risk
Imagine waking up to find your Bitcoin or Ethereum swapped out without a trace, with no scam alert or email notification. That’s the terrifying frontier unlocked by this breach. Among the ~16 billion exposed entries are login credentials and session tokens tied to crypto exchanges, wallets, and trading platforms, from Binance and Coinbase to MetaMask and Trust Wallet. Attackers armed with these tokens can bypass passwords, slip past MFA, and hijack accounts in seconds.
This isn’t theoretical. Cointelegraph warns that this trove "poses serious risks for crypto holders," noting the leak feeds credential-stuffing, phishing, and session hijacking campaigns targeting crypto users. Think of it as handing a stranger a live session key to your exchange, fund transfers, wallet wipes, or crypto theft could happen before you realize it.
If you're active in crypto, this leak isn’t just an email notification; it's a direct threat to your digital wealth. Reset exchange logins, rotate API keys, link hardware wallets, and monitor every wallet and account like it’s your last safeguard.
🕵️♂️ Where Did This Data Come From?
This wasn't a single massive breach like Yahoo or Equifax.
Instead, it’s a mega-compilation from two sources:
1. Infostealer Malware (~85%)
Malware like RedLine, Raccoon, Vidar, often spreads via:
Phishing emails
Pirated software
Fake browser extensions
These tools scrape credentials directly from your system; no need to hack a website.
They capture:
Browser-stored passwords
Session tokens (to bypass MFA)
Clipboard contents, screenshots, and even crypto wallet keys
2. Historical Data Dumps (~15%)
Includes old leaks from:
LinkedIn
RockYou
Dropbox
Adobe
Aggregated into one massive attack-ready database
🧨 Why This Changes Everything?
✅ It's Not Just Passwords Anymore
Cookies, session tokens, and live logins are in the wild.
Attackers can log in as you, even after you change your password.
🧠 It’s Structured for Mass Use
The leak is cleanly organized, enabling:
Credential stuffing
Targeted phishing
Identity theft
Ransom attacks
🎯 It's Fresh
Not just stale, reused passwords.
New, weaponizable data was in these datasets, including recent session tokens.
🔓 MFA (Multi-Factor Authentication) Is Not Enough
If your session token is hijacked, MFA won’t help.
Your active sessions could be used against you.
🛡️ How Big Tech Is Reacting
Not a Google system breach
Urges use of:
Password manager
Passkeys
Security checkups
🍏 Apple & Meta
Encouraging:
Password resets
Passkey migration
Device-based login hardening
None of these giants were directly hacked, but their ecosystems are indirectly endangered.
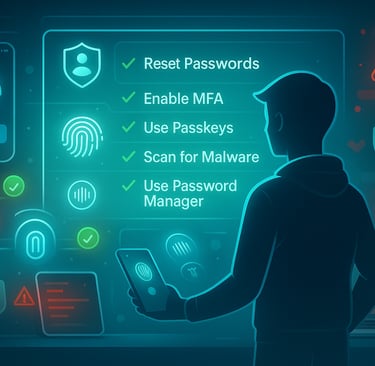
📌 What You Can Do Right Now
1. Reset Critical Passwords
Start with:
Gmail, iCloud, Facebook
Banking, email, crypto
Work accounts (Slack, GitHub, etc.)
Use long, complex, unique passwords.
2. Enable Multi-Factor Authentication (MFA)
Use:
Authenticator apps (e.g., Google Auth, Authy)
Hardware keys (e.g., YubiKey)
Avoid SMS-only if possible
3. Adopt Passkeys
Phishing-resistant and harder to intercept.
Available across:
Google
Apple
Facebook
Amazon
🧾 Final Take
This wasn’t a hack on Google or Meta. It was worse, a silent weaponization of stolen data, now repackaged and leaked at an unprecedented scale.
Over 16 billion login entries, including tokens, cookies, and passwords, are now public. The threat is real and evolving.
🛡️ Your next steps:
Rotate your passwords
Enable MFA or, better, passkeys
Run malware scans
Use breach monitoring tools
Stay alert, stay private
🔗 Reference Links
🔔 Stay Plugged Into the Chain
Don’t just read the future, ride it.
Join crypto-curious minds who are already unlocking insights with us.
📬 Subscribe to our newsletter for weekly alpha, real-world strategies.
📱 Follow us on Instagram and X for bite-sized insights, memes, and market signals that actually make sense.
4. Use a Password Manager
Bitwarden, 1Password, and others:
Generate secure passwords
Warn you of known breaches
Auto-fill for convenience and safety
5. Check If You Were Exposed
Google’s Dark Web Report via your Account Security tab
6. Scan Your Devices
Run:
Malwarebytes
Windows Defender
Norton, Bitdefender, etc.
Especially if you’ve:
Used cracked software
Installed unknown browser extensions
Clicked sketchy ads
7. Review Active Sessions
Sign out of unknown devices
Check session history on Google, Facebook, Apple
8. Stay Suspicious
Ignore shady DMs
Don’t click password reset links you didn’t request
Watch for unusual login alerts
🔮 The Future: From Panic to Preparedness
We're now in a new age of cybercrime:
Infostealer-as-a-Service is booming
Credential markets are well-funded and fast
Session hijacking is the new norm
The Industry Response: Passkeys & Zero Trust
Passkeys remove password reuse risks
Zero-trust architecture assumes every device is suspect
Companies are moving toward token expiration & device fingerprinting
But while companies adapt, you still control your personal security posture.


Subscribe to our newsletter
CIN - ChainInsights Net
Crypto Education & Legacy Platform.
Explore crypto finance, trends, and market strategies.
© 2025 ChainInsights Net. All rights reserved.
⚠️ Disclaimer
Everything you see on ChainInsights.net — including blog posts, tools, links, community content, and socials — is shared for general educational purposes only. We source insights from multiple third-party platforms, but we don’t guarantee the accuracy, completeness, or freshness of the information.
Nothing here is financial, legal, or investment advice. You shouldn’t make decisions based solely on our content. Always do your own deep-dive, triple-check your sources, and consult a qualified financial advisor before putting capital on the line.
Crypto is risky, and markets move fast. Your choices are yours alone — we’re just here to decode the noise, not direct your trades.
❤️ Fuel the Mission
Every world-changing idea starts with someone who believes.
Every movement begins with one spark, but it takes a community to build the fire.
Your support helps us grow, reduce ads, and stay truly free.
Donations: 0x331381fB8AE4894d8Ee8d1f066C4582B2262ccDA